Iran blamed Israel and the United States for disrupting sales at gas stations nationwide on Oct. 26, 2021. The cyberattack disabled a system that allows millions of Iranians to use government-issued cards to buy fuel at a subsidized price. Card users reportedly received the message “cyberattack 64411,” the phone number for a hotline run by Supreme Leader Ayatollah Ali Khamenei’s office.
 The outage affected all of Iran’s 4,300 gas stations. Long lines formed at stations and disrupted traffic in cities. The only way for many customers to buy fuel was to pay the regular rate, more than double the subsidized one. Digital billboards in Tehran and Isfahan were also compromised. Some displayed the message, “Khamenei! Where is our gasoline?” Others read “Free fuel in Jamaran gas station,” probably a reference to the neighborhood where revolutionary leader Ayatollah Ruhollah Khomeini lived.
The outage affected all of Iran’s 4,300 gas stations. Long lines formed at stations and disrupted traffic in cities. The only way for many customers to buy fuel was to pay the regular rate, more than double the subsidized one. Digital billboards in Tehran and Isfahan were also compromised. Some displayed the message, “Khamenei! Where is our gasoline?” Others read “Free fuel in Jamaran gas station,” probably a reference to the neighborhood where revolutionary leader Ayatollah Ruhollah Khomeini lived.
The attack appeared to be the latest in a long string of cyber operations targeting the Islamic Republic since 2010, which Iran has often attributed to Israel and the United States.
President Ebrahim Raisi said that the disruption of fuel sales was meant to anger people by creating disorder. “There should be serious readiness in the field of cyberwar and related bodies should not allow the enemy to follow their ominous aims,” he said on October 27. Raisi visited the oil ministry to follow up on the incident and spoke with workers at a gas station in Tehran. By October 30, some 3,200 out of 4,300 stations had been reconnected to the central distribution system, resuming subsidized sales.

An obscure hacking group called Predatory Sparrow claimed responsibility for the attack. It was in “response to the cyber actions by Tehran's terrorist regime against the people in the region and around the world,” the group said in a Telegram post.
But Iranian officials said that a state actor was probably responsible. “We are still unable to say forensically, but analytically I believe it was carried out by the Zionist regime, the Americans and their agents,” Brigadier General Gholamreza Jalali, the head of Iran’s Civil Defense Organization, said on October 30. Jalali added that the gas station incident resembled two other cyberattacks that Iran also attributed to Israel and the United States:
- In May 2020, a cyberattack disrupted systems that regulate traffic at Iran’s Shahid Rajaei port in the Persian Gulf. The port’s operations were significantly hampered for at least three days.
- In July 2021, hackers caused chaos at train stations nationwide by posting fake messages about cancellations on display boards. The messages also urged passengers to call 64411, the same number featured in the gas station attack. Websites tied to the Transport and Urban Development ministry also went down. (Predatory Sparrow also claimed responsibility for this attack.)
Iran and Israel have been at odds for more than four decades. After the 1979 revolution, the new Islamic regime embraced the Palestinian cause and cut ties with Israel. The conflict evolved into a proxy war as Iran funded, trained and armed militant groups, such as Hezbollah in Lebanon and Hamas in Gaza, on Israel’s borders.
 By 2010, hostilities played out in cyberspace as well. The full scope of the cyber war is unknown, in part because neither country claims responsibility for attacks on the other nation.
By 2010, hostilities played out in cyberspace as well. The full scope of the cyber war is unknown, in part because neither country claims responsibility for attacks on the other nation.
Israel, along with the United States, has been linked to several sophisticated cyberattacks against Iran. Most of the targets have been related to the country’s nuclear program. The first major infiltration attributed to Israel was the infection of computers at Iran’s Bushehr nuclear power plant in 2010. The Stuxnet virus was allegedly developed by Israel and the United States.
After the Stuxnet attack, Iran appeared to invest more resources into its nascent cyber program. It improved both defensive and offensive capabilities. Since the 2010s, hackers linked to Iran have reportedly targeted Israeli officials, defense companies, and even water infrastructure.
“Iran attacks Israel on a daily basis,” then-Prime Minister Benjamin Netanyahu said at a tech conference 2019. “We monitor these attacks, we see these attacks and we foil these attacks all the time.”
By 2019, Tehran considered cyber operations a “safe, low-cost method to collect information and retaliate against perceived threats,” the U.S. Defense Intelligence Agency reported. “Tehran often masks its cyber-operations using proxies to maintain plausible deniability.”
Despite Iran’s progress, Israel was still widely regarded as the more advanced actor. In 2021, the International Institute for Strategic Studies (IISS) ranked the world’s top cyber powers into three tiers based on their capabilities. IISS placed the United States alone in tier one. Israel was in tier two, along with Australia, Britain, Canada, China, France, and Russia. Iran was in tier three, along with India, Indonesia, Japan, Malaysia, North Korea, and Vietnam.
Timeline of Israel-Iran Cyberattacks
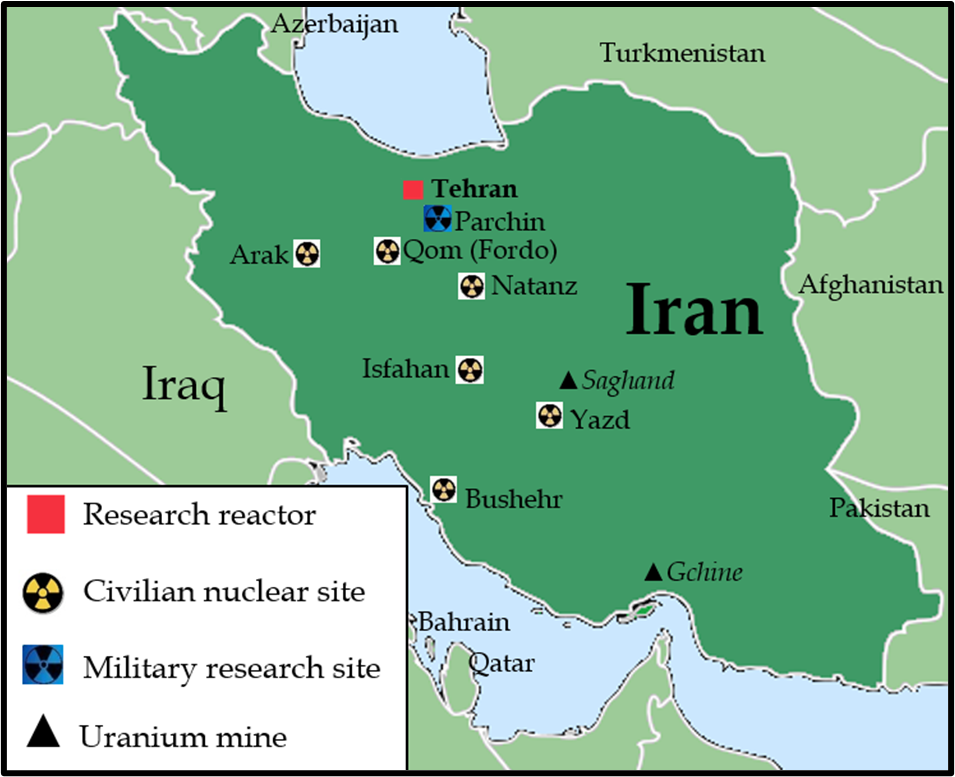 June 2010: The Stuxnet computer virus, allegedly developed by Israel and the United States, was detected in computers at the Bushehr nuclear power plant. The virus then spread to other facilities. By September, 30,000 computers across at least 14 facilities—including the Natanz facility—were reportedly infected. The virus caused the engines in IR-1 centrifuges to increase their speed and eventually explode. At least 1,000 centrifuges of the 9,000 installed at Natanz were destroyed, the Institute for Science and International Security estimated. After conducting investigations, Iran blamed Israel and the United States for the virus.
June 2010: The Stuxnet computer virus, allegedly developed by Israel and the United States, was detected in computers at the Bushehr nuclear power plant. The virus then spread to other facilities. By September, 30,000 computers across at least 14 facilities—including the Natanz facility—were reportedly infected. The virus caused the engines in IR-1 centrifuges to increase their speed and eventually explode. At least 1,000 centrifuges of the 9,000 installed at Natanz were destroyed, the Institute for Science and International Security estimated. After conducting investigations, Iran blamed Israel and the United States for the virus.
April 2011: Iran’s cyber defense agency discovered a virus nicknamed “Stars” that was designed to infiltrate and damage its nuclear facilities. The virus mimicked official government files and inflicted “minor damage” on computer systems, according to Gholam Reza Jalali, the head of Iran’s Passive Defense Organization. Iran blamed the United States and Israel.
Nov. 13, 2011: Iran said it had contained Duqu, the third virus aimed at disrupting Iran’s nuclear program. Duqu used programming code that was also used in the 2010 Stuxnet attack.
April 2012: Iran discovered the “Wiper” malware erasing the hard drives of computers owned by the oil ministry and the National Iranian Oil Company. “Wiper” appeared to be similar in design to Duqu and Stuxnet, thought to have been developed by Israel and the United States. Iran blamed the United States and Israel for the attack.
May 2012: Iran announced that a virus dubbed “Flame” had infected government computers and had tried to steal government data. Israel and the United States had deployed the Flame virus to collect intelligence and to prepare for a wider cyberwarfare campaign, The Washington Post reported. In Israel, Vice Prime Minister Moshe Yaalon did not confirm the nation’s involvement but acknowledged that Israel would use “all means... to harm the Iranian nuclear system.”
July 2012: Iranian hackers targeted Israeli government officials with a cyber espionage tool nicknamed Madi. The malware logged keystrokes, recorded audio, and stole documents.
February 2013: Symantec Corp researchers found pieces of Stuxnet code that had been used to infiltrate systems at Natanz in November 2007, some two years earlier than previously reported. But the researchers could not determine if the earlier version of the virus had caused any damage.
June 2015: Security experts in Israel discovered a cyberespionage campaign that started in 2012. Hackers using malware – dubbed “Explosive” by the security company Check Point – tried to steal data from military suppliers, media agencies, telecommunications firms, and universities in about a dozen countries. Researchers said the attack appeared to be the work of Hezbollah and an Iranian hacker.
June 2015: The cybersecurity company ClearSky discovered a widespread “phishing” operation targeting over 500 academic researchers in Israel, Saudi Arabia and other Middle Eastern countries. The cyberespionage dated as far back as 2011 and was linked to Iranian interests.
April 2017: The Iranian hacker group OilRig attempted to launch a cyberespionage operation against over 250 Israeli targets. The hackers tried to use a vulnerability in Microsoft Word to gain access to the systems of government officials and computing companies. Israel’s Cyber Defense Authority thwarted the attack. Cybersecurity experts said that the attempt showed that the hackers were using increasingly sophisticated methods. “This is one of the more advanced fileless campaigns I’ve seen,” Michael Gorelik, vice president of Israeli security firm Morphisec, said. “It was a targeted, large campaign using quite a big infrastructure.”
Oct. 28, 2018: The head of Iran’s civil defense agency claimed that it had neutralized a “new generation” of the Stuxnet virus attempting to damage communications infrastructure. Iranian officials blamed Israel for the attack. “Thanks to our vigilant technical teams, it failed,” Telecommunications Minister Mohammad Javad Azari Jahromi said.
March 2019: Before Israel’s parliamentary election, Iranian intelligence allegedly hacked the phone of Benny Gantz, leader of the Blue and White party.
April 2020: Iran reportedly hacked into Israel’s Water Authority systems to increase chlorine levels in water for residential use. Water pumps at a station in southern Israel malfunctioned, but the water supply was not contaminated.
May 9, 2020: A cyberattack hit computers that regulate maritime traffic at Shahid Rajaee port on Iran's southern coast in the Persian Gulf. The disruption created a traffic jam of ships that waited days to dock. Iran acknowledged that it had been hit by a foreign hack. Israel was reportedly behind the cyberattack, although it did not claim responsibility, according to The Washington Post.
September-October 2020: A hacker group allegedly linked to Iran targeted “many prominent Israeli organizations” in September, according to two Israeli cybersecurity companies. Clearsky and Profero, the firms, said that they had thwarted the large-scale operation launched by MuddyWater, a group that previously worked for Iran’s Revolutionary Guards. MuddyWater had used malware disguised as ransomware. The virus was designed to encrypt files and demand payment, “but the malware was modified so that it could not revert and decrypt the files,” according to a report by Clearsky.
March 30, 2021: The hacking group dubbed Charming Kitten (aka Phosphorous) had targeted two dozen medical researchers in the United States and Israel, the cybersecurity group Proofpoint reported. Iranian hackers impersonated a prominent Israeli physicist and sent spear phishing emails to medical professionals.
April 11, 2021: An explosion at Natanz hit the power supply for centrifuges and caused damage that could take up to nine months to fully repair, The New York Times reported. Alireza Zakani, head of Parliament’s Research Center, said that “thousands of centrifuges” were destroyed during the blackout. He claimed that 300 pounds of explosives had been smuggled into the facility in equipment that had been sent abroad for repair.
American and Israeli intelligence officials told The New York Times that Israel played a role in the sabotage. Unnamed intelligence sources told Israeli media that the Mossad was responsible for a cyberattack that caused the blackout.
May 2021: A hacking group dubbed Agrius had been launching cyberattacks on Israeli targets since December 2020, SentinelLabs researchers reported. The group, allegedly linked to Iran, tried to deploy malware that would erase data on infected devices.
May 2021: A hacking group called N3tw0rm launched ransomware attacks against H&M Israel and other Israeli companies. The group appeared to be related to Pay2Key, an Iran-linked group that claimed previous attacks on Israel Aerospace Industries and the Israeli cybersecurity company Portnox.
July 9-10, 2021: On July 9, hackers caused chaos at train stations nationwide by posting fake messages about cancellations on display boards. The messages urged passengers to call 64411, the number for a hotline run by the Supreme Leader’s office. On the next day, websites tied to the Ministry of Roads and Urbanization reportedly went down. Iran blamed Israel and the United States.
An Israeli-American cybersecurity company, however, concluded that Indra, a group of hackers who identify as opponents of Iran’s theocratic regime, was most likely responsible. The code used in the attack resembled code in previous attacks claimed by the group in 2019 and 2020.
Oct. 11, 2021: Microsoft announced that a hacking group linked to Iran attempted to gain access to more than 250 accounts “with a focus on U.S. and Israeli defense technology companies, Persian Gulf ports of entry, or global maritime transportation companies with business presence in the Middle East.” Some of the targeted companies produce drones, military-grade radars and other advanced equipment. Fewer than 20 of the targets were compromised.
Microsoft stopped short of attributing the attacks to the Iranian government but said that the “activity likely supports the national interests of the Islamic Republic.” The techniques and targets matched those of another hacking group originating in Iran.
Oct. 26, 2021: A cyberattack knocked out the system that allows Iranians to use government-issued cards to purchase fuel at a subsidized rate. The outage impacted all 4,300 gas stations in Iran. Consumers either had to pay the regular price, more than double the subsidized one, or wait for stations to reconnect to the central distribution system. By October 30, some 3,200 out of 4,300 stations had been reconnected to the system. Iran blamed Israel and the United States.
Feb. 23, 2022: Iran’s Revolutionary Guards published footage from security cameras at two key Israeli ports, Ashdod and Haifa. They also published a file with personal information on hundreds of port workers. Representatives of the ports told Israeli media, however, that the footage was obtained by hacking a company that operated the cameras. So the equipment had not been compromised. The ports also said that footage was old.
July 30, 2023: Israel foiled an Iranian phishing operation that targeted government employees and nongovernment experts on LinkedIn, the Shin Bet intelligence organization said. Iranian agents posed as colleagues on LinkedIn and tried sending Israeli targets corrupted files that would compromise their computers.
Garrett Nada, managing editor of "The Iran Primer" assembled this report with research support from Tess Rosenberg, a research analyst at the U.S. Institute of Peace, and Brett Cohen, a research assistant at the Woodrow Wilson Center. Part of the timeline was based on prior work by Andrew Hanna.
