Groups linked to Iran’s government have stepped up efforts to interfere in the 2024 U.S. election, according to a Microsoft report released on Aug. 9, 2024. They have spread disinformation and polarizing messages using covert news sites and social media. The goal appeared to be to sow chaos and undermine trust in authorities and elections. Also, a hacking group managed by the Revolutionary Guards intelligence unit sent a spear-phishing email to a high-ranking official of a presidential campaign.
In July 2024, U.S. intelligence had reported that Iran was running influence operations to undermine former President Donald Trump’s campaign. Tehran was “working to influence the presidential election, probably because Iranian leaders want to avoid an outcome they perceive would increase tensions with the United States,” the Office of the Director of National Intelligence said in a statement. The following are excerpts from the Microsoft Threat Intelligence Report.
Iran steps into US election 2024 with cyber-enabled influence operations
Foreign malign influence concerning the 2024 US election started off slowly but has steadily picked up pace over the last six months due initially to Russian operations, but more recently from Iranian activity. This third election report from the Microsoft Threat Analysis Center (MTAC) provides an update on what we’ve observed from Russia, Iran, and China since our second report in April 2024, “Nation-states engage in US-focused influence operations ahead of US presidential election.”
Over the past several months, we have seen the emergence of significant influence activity by Iranian actors. Iranian cyber-enabled influence operations have been a consistent feature of at least the last three US election cycles. Iran’s operations have been notable and distinguishable from Russian campaigns for appearing later in the election season and employing cyberattacks more geared toward election conduct than swaying voters. Recent activity suggests the Iranian regime—along with the Kremlin—may be equally engaged in election 2024.
Iran enters the fold with cyber-influence operations starting June 2024
Iranian actors have recently laid the groundwork for influence operations aimed at US audiences and potentially seeking to impact the 2024 US presidential election. This recent cyber-enabled influence activity arises from a combination of actors which are conducting initial cyber reconnaissance and seeding online personas and websites into the information space.
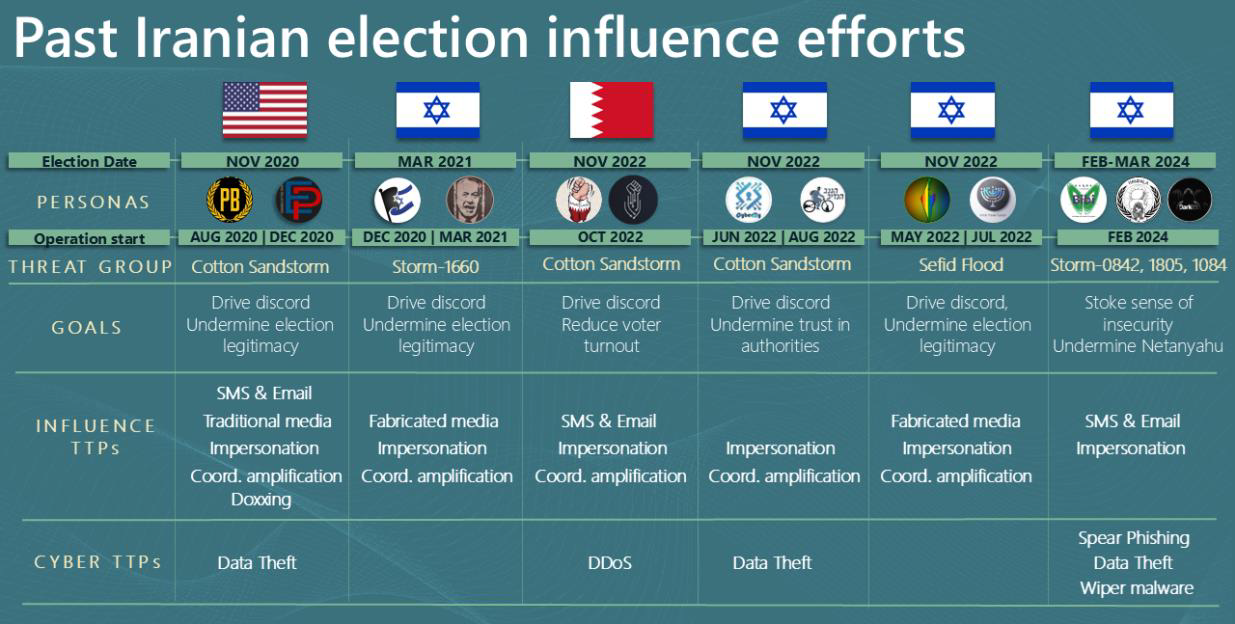
Cyber-enabled influence operations aimed at US and other global elections have been a persistent target for Iran in recent years. As we noted in our first elections report last November 2023, “during the 2020 US presidential election, Iran launched multiple cyber-enabled influence operations that impersonated American extremists, and attempted to sow discord among US voters and incite violence against US government officials. Since 2020, Iran extended its track record of election meddling, amplifying cyberattacks with parallel online influence operations in Bahrain and Israel.” As seen in Figure 1 below, Iran has employed fabricated media, impersonations and in many cases cyberattacks throughout the last four years targeting the US, Bahrain, and Israel.
Looking forward, we expect Iranian actors will employ cyberattacks against institutions and candidates while simultaneously intensifying their efforts to amplify existing divisive issues within the US, like racial tensions, economic disparities, and gender-related issues. Here’s what we’ve seen thus far in 2024 from Iranian actors with respect to the upcoming US election.
Sefid Flood prepares for possible influence operations
Sefid Flood, an Iran-linked influence actor, began staging for influence operations in the 2024 US elections following the Iranian New Year in late March. Sefid Flood specializes in impersonating social and political activist groups in a target audience to stoke chaos, undermine trust in authorities, and sow doubt about election integrity. This group’s operations may go as far as intimidation, doxing, or violent incitement targeting political figures or social/political groups.
IRGC threat actors enter preparatory stage for likely cyber-enabled influence
In June 2024, Mint Sandstorm—a group run by the Islamic Revolutionary Guard Corps (IRGC) intelligence unit—sent a spear-phishing email to a high-ranking official of a presidential campaign from a compromised email account of a former senior advisor. The phishing email contained a fake forward with a hyperlink that directs traffic through an actor-controlled domain before redirecting to the listed domain. Mint Sandstorm similarly targeted a presidential campaign in May and June 2020 five to six months ahead of the last US presidential election.
On June 13, Mint Sandstorm also unsuccessfully attempted to log in to an account belonging to a former presidential candidate. Mint Sandstorm’s target selection and timing—days prior to phishing an active presidential campaign and months ahead of the election—suggest their attempted authentication may also be election-related. Given Mint Sandstorm’s regular targeting of senior political officials for intelligence collection unrelated to elections, additional evidence is required to make a determination. Regardless of the intent, this targeting is a reminder that senior policymakers should be cognizant of monitoring and following cybersecurity best practices even for legacy or archived infrastructure, as they can be ripe targets for threat actors seeking to collect intelligence, run cyber-enabled influence operations, or both.
In May, Peach Sandstorm (a.k.a. APT-33)—another group with assessed links to the IRGC—compromised a user account with minimal access permissions at a county-level government in a swing state. The compromise was part of a broader password spray operation from the group, and Microsoft Threat Intelligence did not observe any lateral movement or privilege escalation, making it difficult to determine whether it was election-related. While unclear if related, it is worth noting that the targeted county had undergone a race-related controversy that made national news this year. Since early 2023, Peach Sandstorm’s operations have focused on strategic intelligence collection particularly in satellite, defense, and pharmaceutical sectors with some targeting of US government organizations, often in swing states.
Iran-run covert news sites target US voter groups
An Iranian network, Storm-2035, comprising four websites masquerading as news outlets is actively engaging US voter groups on opposing ends of the political spectrum with polarizing messaging on issues such as the US presidential candidates, LGBTQ rights, and the Israel-Hamas conflict. This group is part of a broader campaign that has been operating since at least 2020 and includes over a dozen covert news sites targeting French, Spanish, Arabic, and English-speaking audiences with social and political content.
In 2022, Mandiant reported on one of the news sites, EvenPolitics, noting that the site had published articles discussing the 2022 US midterm elections. An inauthentic amplification network promoting the website was taken down by the X platform in 2022, but the site remains active, publishing around ten articles a week.
A more recently created site, Nio Thinker, first began publishing in late October 2023. The site’s early publications focused on the Israel-Hamas conflict, but have increasingly shifted to the US elections in recent months. Its content caters to liberal audiences and includes sarcastic, long-winded articles insulting Trump including calling him an “opioid-pilled elephant in the MAGA china shop” and a “raving mad litigiosaur”1 (see Figure 2).
Another site, Savannah Time, claims to be a “trusted source for conservative news in the vibrant city of Savannah.” The site focuses heavily on Republican politics and LGBTQ issues, particularly gender re-assignment. MTAC has not observed significant social media amplification of these sites as of yet, though it is possible they will begin closer to election day.
MTAC found evidence indicating the sites are using AI-enabled services to plagiarize at least some of their content from US publications. Examination of webpage source code and indicators in the articles themselves suggest the sites’ operators are likely using SEO plugins and other generative AI-based tools to create article titles, keywords, and to automatically rephrase stolen content in a way that drives search engine traffic to their sites while obfuscating the content’s original source.
