By 2020, tensions between the United States and Iran increasingly played out in invisible cyberspace. Both governments acknowledged that cyberattacks were central to their strategies. The scope was unknown, but cyberspace has turned into a virtual battlefield. Cyber offered an alternative to kinetic military action that could lead to full-scale war – which both Washington and Tehran sought to avoid.
On July 23, the Foreign Ministry acknowledged that the longstanding cyber campaign against Iran’s infrastructure had escalated in recent months. “A couple of cyberattacks on a broader scale have been launched against the country’s infrastructure,” Foreign Minister Seyed Abbas Mousavi told reporters. Given the sophisticated technology used, “one can say they have been sponsored or launched by [foreign] governments.”
Iran has identified the perpetrators “sponsoring and directing the attacks – in some cases the sponsor state – and the groups aiding and abetting the attacks,” he added. “Given Mr. Trump’s order, it would be perfectly natural to say that the U.S. government will be the prime suspect for any cyberattack against Iran hereafter, unless the contrary is proved.” In September 2018, President Trump reportedly granted the CIA more authority to conduct cyberattacks on civilian infrastructure.

U.S. cyberwarfare specialists training at the Warfield Air National Guard Base in Maryland
Mousavi claimed that the attacks had failed or been “repulsed by our defense systems and the cyber incident response teams.” Iran has nonetheless vowed retaliation for the “illegal and criminal order and for proving the U.S. government’s liability,” Mousavi said. “We reserve the right to legitimate defense and proportional and appropriate response to the aggression and harm against our country in the face of cyber and non-cyber attacks.” The Islamic Republic will “employ any tool to defend ourselves,” including cyber and “other weaponry.” The scope of the attacks “is a worrying issue for the entire world, and the international community must give an appropriate response to it,” he added.
Sustained U.S. cyber activities against Iran are widely traced to a covert campaign code-named Operation Olympic Games. Started in 2006 under the Bush administration, the program targeted Iranian nuclear capabilities. President Obama expanded Olympic Games to include the use of offensive cyber weapons against Iran’s nuclear enrichment facilities. In 2010, the Stuxnet virus, allegedly designed by the United States and Israel, seriously damaged the Natanz uranium enrichment facility.
After Trump’s order widening the CIA’s authority to launch cyberattacks, the United States stepped up its cyber efforts against Iran. In June 2019, the Trump administration retaliated against Iran’s downing of a U.S. drone with a cyberattack on a Revolutionary Guard (IRGC) database used to plan attacks on tankers. The United States struck again in September 2019 after Iran allegedly launched drones and cruise missiles on two Saudi oil facilities. Iran, in turn, has ramped up its efforts to penetrate U.S. “soft” targets and email accounts.
Iranian hackers targeted U.S. citizens in the lead up to the 2020 U.S. presidential election. In October 2019, Microsoft warned that an Iranian-government hacker group had tried to breach e-mail accounts associated with journalists, current and former U.S. government officials and a U.S. presidential campaign. And in June 2020, Google said that Iran tried and failed to breach e-mail accounts associated with President Donald Trump’s reelection campaign.
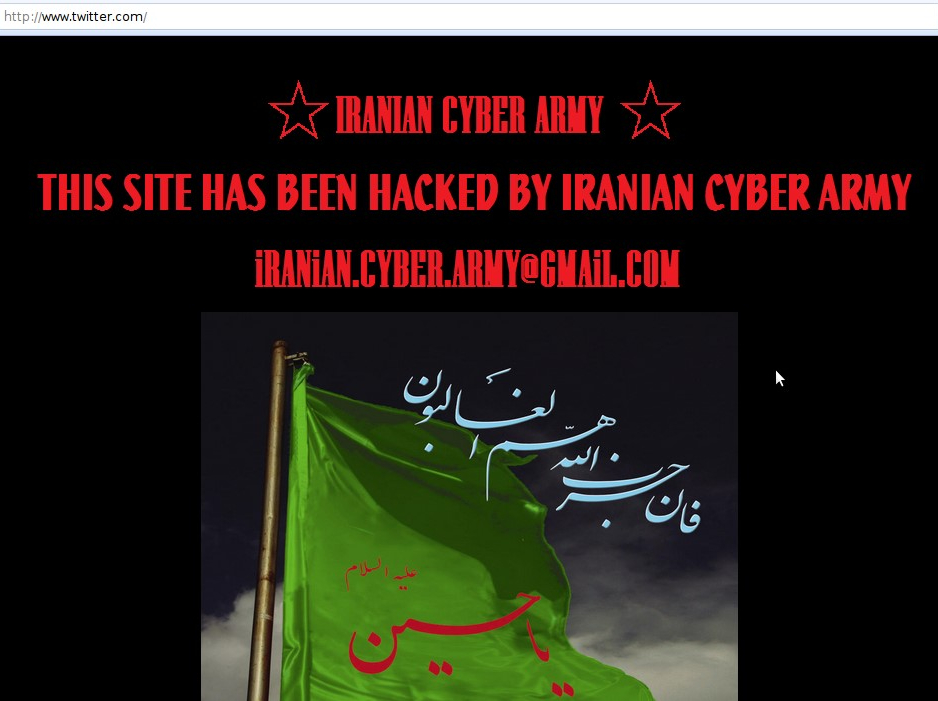
Screenshot of the Twitter homepage in December 2009
Iranian cyberattacks against the United States date back to 2009, when the so-called “Iranian Cyber Army” defaced Twitter’s homepage in response to the Green Revolution protests over alleged fraud in the reelection of President Mahmoud Ahmadinejad.
Iranian cyber activities against the U.S.
Since 2009, Iran’s cyber capabilities have since grown in sophistication and scope. Iran has primarily targeted the private sector rather than U.S. government systems. In September 2012, Iranian hackers directed a Distributed Denial of Service (DDoS) attack against U.S. banks. The campaign, nicknamed Operation Ababil, blocked access to the websites of major financial institutions by overwhelming their servers with web traffic. The attacks cost Western firms millions in lost business, according to a Department of Justice indictment.
Tehran appeared to accelerate its cyber operations against the United States government and its regional partners after the election of President Donald Trump. In August 2017, a cyberattack tied to Iran nearly triggered an explosion at a Saudi petrochemical plant. In December 2018, the Department of Justice indicted two Iranian hackers for a ransomware attack that had crippled Atlanta’s city government in March of that year. The attack locked the files of 8,000 municipal employees and took offline local government operations for nearly a week.
These attacks have coincided with increased Iranian online espionage. In May 2018, cybersecurity firm CrowdStrike warned its clients about a “notable” increase in Iranian phishing activity a day after President Trump’s withdrawal from the JCPOA nuclear deal. Before Israel’s election in March 2019, Benny Gantz, leader of the Blue and White party, reportedly had his phone hacked by Iranian intelligence. Iranian hackers – dubbed “Charming Kitten” by ClearSky Cyber Security – successfully breached the Google account of a U.S. Navy official; they unsuccessfully targeted the personal accounts of State Department employees, according to an IBM cybersecurity report.
On January 4, 2020, the Department of Homeland Security (DHS) warned of a potential Iranian cyberattack in the aftermath of the death of Qods Force commander Qassem Soleimani. The agency said a retaliatory cyberattack by Iran or its proxies could “come with little to no warning” in a bulletin posted to its website. Although DHS said it had “no information indicating a specific, credible threat to the Homeland,” Iran and Hezbollah had the “intent and capability” to conduct a cyberattack within the United States. Later that day, cyber vandals claiming affiliation with Iran defaced the website of the Federal Depository Library Program and threatened further attacks.
U.S. cyber activities against Iran
Since 2006, the United States has ramped up its cyber offensive operations against Iranian government computer systems. The most famous cyberattack was the unleashing of the Stuxnet virus on Natanz, which damaged nearly 1,000 centrifuges and infected 30,000 computers. Iran was forced to take tens of thousands of computers offline. Other cyberattacks—including the Flame and Wiper, viruses reportedly part of Operation Olympic Games—targeted Iran’s oil infrastructure.
U.S. sailors at the Fleet Operations Center at U.S. Fleet Cyber Command
The Trump administration accelerated cyber operations in response to Iranian attacks in the Persian Gulf. In June 2019, United States conducted a cyberattack on Iran after it downed a U.S. drone near the Strait of Hormuz. The attack wiped clean an IRGC database used to plan attacks against tankers in the Persian Gulf. Netblocks, a cyber monitoring firm, also reported widespread internet disruption in Iran after the drone attack.
In September 2019, the United States carried out a cyberattack against unspecified Iranian “physical hardware” – equipment used to disseminate propaganda – after Iran’s attacks on two Saudi oil facilities. The unusual U.S. confirmation of its attacks in October suggested the goal was deter Iran without resorting to kinetic strikes.
In October 2020, the United States seized 92 domains owned by the Revolutionary Guards. Four websites pretended to be reputable news organizations but were "Iranian propaganda to influence United States domestic and foreign policy." The FBI worked with Google, Facebook and Twitter to identify and take down the websites.
Known Iranian Hacker Groups
These names are given by U.S. cybersecurity companies tracking Iranian cyber activity. The U.S. government refers to these groups as "advanced persistent threats" (APTs).
Izz ad-Din al-Qassam Cyber Fighters – This group claimed responsibility for the DDoS cyberattacks against U.S. financial institutions in September 2012. The same month, Sen. Joe Lieberman claimed that the group was connected to the IRGC’s elite Qods Force.
APT33 (aka Elfin, Refined Kitten, Holmium) – This group carried out cyber espionage operations against aviation, military, and energy targets in the United States, Saudi Arabia and South Korea. Cybersecurity firm FireEye linked APT33 to the Iranian government.
APT35 (aka Phosphorous, Charming Kitten, Ajax Security) – This group attempted to breach the e-mail accounts of the Trump re-election campaign in 2019, as well as accounts of U.S. government officials, journalists, and Iranians living outside Iran. Microsoft linked Phosphorous with the Iranian government.
APT39 (aka Remix Kitten, Remexi, Cadelspy, Chafer, Cobalt Hickman and ITG07) – This group has stolen personnel and private business information from telecommunications companies and airlines. It has been active since at least 2014. The Treasury sanctioned APT39 on September 17, 2020.
OilRig – This group focused on private industry targets outside of Iran, most famously hacking Sheldon Adelson’s Las Vegas Sands Corporation in February 2014. The group was, in turn, hacked by Turla, a Russian FSB-associated group. The Russians used the hijacked group to hack targets in the Middle East and the United Kingdom, according to U.S. and British officials in October 2019.
Iranian Dark Coders Team – This hacking collective primarily focused on cyber-vandalism. It defaced American and Israeli websites with pro-Hezbollah and pro-Iran propaganda in 2012. The group has not been tied to the Iranian government and may consist of freelancers or criminal elements.
Timeline of U.S.-Iran Cyberattacks
December 18, 2009 – Twitter’s homepage was hacked and defaced by a group claiming to be the “Iranian Cyber Army” in response to the Green Revolution protests.
July 2010 – The Stuxnet virus was identified by a Belorussian computer security company. Subsequent technical analysis showed the malware was likely created to target Iranian industrial facilities.
September 25, 2010 – Iran’s Atomic Energy Organization said it was fighting malware that targeted its nuclear facilities. An Iranian official said 30,000 computers had been infected by Stuxnet.
April 25, 2011 – Iran’s cyber defense agency discovered a virus nicknamed “Stars” that was designed to infiltrate and damage its nuclear facilities.
April 23, 2012 – Cyberattacks forced Iran to take several oil terminals offline. The virus, nicknamed “Wiper,” spread through the Iranian Oil Ministry and National Iranian oil Company.
May 2012 – Iran acknowledged that a virus dubbed “Flame” had infected government computers and was capable of stealing data.
June 19, 2012 – Western officials told The Washington Post that the United States and Israel had deployed the Flame virus to collect intelligence on Iranian computer networks in order to prepare for a cyberwarfare campaign.
July 2012 – Iranian hackers targeted Israeli government officials with a cyber espionage tool nicknamed Madi. The malware logged keystrokes, recorded audio, and stole documents.
August 2012 – The Shamoon virus erased three-quarters of all corporate computers owned by Saudi Aramco and replaced the data with an image of a burning American flag. U.S. officials blamed Iran for the cyberattack.
September 11, 2012 – A group called the Izz ad-Din al-Qassam Cyber Fighters directed a DDoS attack against U.S. banking infrastructure in a cyber campaign named Operation Ababil.
October 12, 2012 – U.S. official blamed Iranian hackers with ties to the government for attacks against U.S. banks and Saudi oil facilities.
January 8, 2013 – U.S. officials blamed Iran for the Operation Ababil banking cyberattacks.
September 27, 2013 – Iranian hackers compromised unclassified U.S. Navy computers in the midst of talks over Iran’s nuclear program.
February 2014 – Iranian hackers targeted Sheldon Adelson’s Las Vegas Sands Corp. The attack shut down communications systems and wiped hard drives clean.
November 2015 – IRGC hackers targeted State Department and other Obama administration officials.
March 24, 2016 – The Department of Justice indicted seven Iranian hackers for cyberattacks against U.S. banks and a New York dam. It claimed the hackers worked on behalf of the Iranian government and the IRGC.
November 11, 2016 – The Shamoon virus resurfaced in Saudi Arabia, according to Symantec.
January 2017 – An updated Shamoon virus targeted Saudi government computer systems at petrochemical plants.
August 2017 – A failed cyberattack attempted to trigger an explosion at a Saudi petrochemical company.
March 22, 2018 – A ransomware attack known as SamSam crippled Atlanta’s city government.
May 9, 2018 – Cybersecurity firm CrowdStrike warned about a “notable” increase in Iranian cyberactivity within 24 hours of the Trump administration’s withdrawal from the JCPOA.
July 20, 2018 – U.S. senior officials warned Iran had prepared for extensive cyberattacks against the United States and European infrastructure.
September 2018 – The Trump administration allegedly issued a presidential finding that allowed the CIA to conduct more aggressive cyberattacks against Iranian critical infrastructure.
October 28, 2018 – The head of Iran’s civil defense agency claimed it had neutralized a “new generation of Stuxnet” attempting to enter the country’s communications infrastructure. Iranian officials blamed Israel for the attack.
December 5, 2018 – The Department of Justice indicted two Iranian nationals for the SamSam ransomware attack against the city of Atlanta.
January 2019 – Cybersecurity firm FireEye detailed a two-year campaign by Iran to steal login credentials and business details in the Middle East, Europe and North America.
March 6, 2019 – Microsoft said Iranian cyberattacks had targeted over 200 companies in the past two years.
April 2019 – A hack against Iranian data centers left a U.S. flag on Iranian computer screens along with a message not to interfere with American elections.
June 17, 2019 – Tehran claimed it dismantled a CIA-run cyber espionage network in Iran.
June 20, 2019 – The United States conducted a cyberattack after Iran’s attacks against oil tankers in the Strait of Hormuz and downing of a U.S. drone. U.S. officials later told The New York Times that the attacks wiped clean an IRGC database used to plan the tanker attacks.
June 22, 2019 – The Department of Homeland Security said Iran had increased its “malicious cyber activity” against U.S. government agencies and private industry.
June 26, 2019 – Netblocks reported widespread internet disruption in Iran.
July 17, 2019 – Microsoft said nearly 10,000 customers were targeted by state-sponsored cyberattacks from Iran, Russia, and North Korea
September 2019 – The United States conducted a cyberattack against Iran in retaliation for a drone and missile attack against Saudi oil facilities. U.S. officials told Reuters the operation targeted physical hardware related to Iran’s ability to disseminate propaganda.
October 4, 2019 – Microsoft said that Iranian hacker group Phosphorous tried to breach accounts associated with U.S. presidential campaigns. The hackers failed to breach accounts connected with President Trump’s re-election campaign as well as the accounts of journalists and U.S. officials.
October 22, 2019 – Court documented revealed that the FBI tracked Iranian hackers who had breached American satellite technology companies.
January 25, 2020 – The United States blocked access to “farsnews.com,” the English language web address for the Revolutionary Guard-affiliated Fars News Agency.
February 8, 2020 – Netblocks reported that national internet connectivity in Iran fell to 75 percent after Iran activated cyber countermeasures to a DDoS attack.
April 2020 – Hackers linked to Iran reportedly conducted a phishing attack against top executives at Gilead Sciences Inc, a U.S. drugmaker. Cybersecurity researchers at Israeli cybersecurity firm ClearSky traced the web domain and servers employed in the attack back to Iran.
June 4, 2020 – Google said that Iranian hackers with APT 35 conducted a phishing attack against President Trump’s reelection campaign. The hackers failed to gain access to any staffer email accounts.
July 16, 2020 – IBM said that Iranian hackers with APT 35/Charming Kitten breached the Google account of a U.S. Navy official and targeted State Department employees with phishing attacks.
September 2, 2020 – The Justice Department took down two domains - “Aletejahtv.com” and “Aletejahtv.org”- affiliated with Kataib Hezbollah, an Iranian-backed militia in Iraq.
September 17, 2020 – The Treasury sanctioned two groups for cyber espionage. The new sanctions covered Rana Intelligence Computing Company, an Iranian cyber firm, and a cyber espionage group dubbed “Advanced Persistent Threat 39 (APT 39)” by U.S. cyber security companies. The Treasury also designated 45 individuals employed by Rana. All were allegedly working – directly or indirectly – for the Ministry of Intelligence and Security (MOIS).
September 30, 2020 – Twitter removed 150 accounts that it said "appeared to originate in Iran" and were "attempting to disrupt the public conversation during the 2020 U.S. presidential debate."
We identified these accounts quickly, removed them from Twitter, and shared full details with our peers, as standard. They had very low engagement and did not make an impact on the public conversation. Our capacity and speed continue to grow, and we'll remain vigilant. Samples ⬇️ pic.twitter.com/1qzzL8l29H
— Twitter Safety (@TwitterSafety) October 1, 2020
October 7, 2020 – The United States seized 92 domain names used by the Revolutionary Guards to spread disinformation. Four of the domain names "purported to be genuine news outlets but were actually controlled by the IRGC and targeted the United States for the spread of Iranian propaganda," the Justice Department said.
October 15, 2020 – Tehran confirmed two cyberattacks against government targets that occurred from October 12-13. Iran's port authority claimed that it thwarted an attack against the agency's electronic systems. Several agencies temporarily suspended services and conducted technical tests after the attacks were reported.
October 20, 2020 – A hacker group with alleged ties to Iran targeted "many prominent Israeli organizations" in September, according to two Israeli cybsersecurity companies. Clearsky and Profero reported that the group, named MuddyWater, had used malware "disguised as ransomware." The virus would encrypt files and demand payment, "but the malware was modified so that it could not revert and decrypt the files," the report said.
October 28, 2020 – An Iranian cybergroup known as Phosphorus targeted attendees of the Munich Security Conference and the Think 20 Summit in Saudi Arabia, according to Microsoft. The hacker group sent fake invitations to attendees. It successfully comprised the accounts of "former ambassadors and other senior policy experts" before Microsoft detected the attacks.
October 30, 2020 – An Iranian cybergroup targeted U.S. state election websites and "successfully obtained voter registration data in at least one state," according to the Federal Bureau of Investigation (FBI) and the Cyber Security & Infrastructure Agency (CISA). Iran obtained "non-public voter data" but were not able to "alter any voter data in the state system," the two agencies said in a joint statement.
November 3, 2020 – U.S. Cyber Command and the National Security Agency targeted Iranian hackers ahead of the U.S. presidential election.
November 4, 2020 – The United States took down 29 websites used by the Revolutionary Guards that sought to "covertly influence United States policy and public opinion," the Justice Department said.
December 3, 2020 – CISA issued a "heightened awareness" alert for Iranian cyberattacks. They warned about Iran's range of capabilities, including "website defacement, distributed denial of service (DDoS) attacks, and theft of personally identifiable information...social media-driven influence operations, destructive malware, and, potentially, cyber-enabled kinetic attacks."
February 23, 2021 – Twitter removed 238 accounts operating from Iran after completing an investigation into Iranian efforts to interfere in the 2020 presidential election. The accounts were suspended for "various violations of our platform manipulation policies," the social media company said.
March 16, 2021 – The Office of the Director of National Intelligence said that it had "high confidence" that Supreme Leader Ayatollah Ali Khamenei authorized a cyber influence campaign during the 2020 presidential election. The online operation was intended to "undercut former President Trump's reelection prospects - though without directly promoting his rivals." Iranian cyber actors published more than 1,000 pieces of online content from several thousand fake social media accounts. Iran also sent threatening emails to Democratic voters, tried to exploit vulnerabilities on state election websites and attempted to hack the email accounts of political campaign officials.
March 30, 2021 – Charming Kitten (aka Phosphorous) had targeted two dozen medical researchers in the United States and Israel, the cybersecurity group Proofpoint reported. Iranian hackers impersonated a prominent Israeli physicist and sent spearphising emails to medical professionals.
June 22, 2021 – The United States seized three dozen web addresses affiliated with Iran and its proxies, including Tehran’s flagship international broadcaster Press TV. Thirty-three websites operated by the Iranian Islamic Radio and Television Union (IRTVU) had conducted "disinformation campaigns and malign influence operations," the Justice Department said in a statement. Three others were used by Kataib Hezbollah, an Iraqi Shiite militia group backed by Iran’s Revolutionary Guards.
July 15, 2021 – Facebook took down nearly 200 fake accounts used by Iranian hackers to target U.S., British and European military and defense personnel. The hackers, known as Tortoiseshell, sought to infect victims’ computers with malware and steal their login information. The malware used by the hackers was developed by Mahak Rayan Afraz (MRA), “an [information technology] company in Tehran with ties to the Islamic Revolutionary Guard Corps (IRGC),” according to Facebook’s cybersecurity team.
The hackers, known as Tortoiseshell, posed as recruiters for the defense and aerospace industries, as well as employees in the hospitality industry, medicine, journalism, NGOs and civilian airliners. They reached out to their targets online to "build trust and trick them into clicking on malicious links," Facebook said in a statement. The hackers also ran several fake job recruiting websites, including one that mimicked the U.S. Department of Labor's job website, to steal their victims' login credentials. "This activity had the hallmarks of a well-resourced and persistent operation, while relying on relatively strong operational security measures to hide who’s behind it," the statement said.
July 26, 2021 – Five documents allegedly outlining Iran's research on offensive cyber operations were leaked to Sky News. The reports were reportedly compiled by Intelligence Team 13, a group within the Revolutionary Guard's cyber unit, Shahid Kaveh. They detailed how Iran planned to hack critical infrastructure, including water filtration, fuel supply systems and maritime communications. One report examined vulnerabilities in "smart" building management systems in the United States, France and Germany.
Oct. 11, 2021 – Microsoft announced that a hacking group linked to Iran attempted to gain access to more than 250 accounts “with a focus on U.S. and Israeli defense technology companies, Persian Gulf ports of entry, or global maritime transportation companies with business presence in the Middle East.” Some of the targeted companies produce drones, military-grade radars and other advanced equipment. Less than 20 of the targets were compromised since July 2021.
Microsoft stopped short of attributing the attacks to the Iranian government but said that the “activity likely supports the national interests of the Islamic Republic.” The techniques and targets matched those of another hacking group originating in Iran.
Nov. 17, 2021 – U.S., Australian and British cybersecurity agencies said that an Iran-backed hacking group was targeting the transportation and healthcare sectors in the United States as well as Australian organizations. The hackers were trying to access firms’ computer networks by exploiting vulnerabilities in software developed by Microsoft and Fortinet (a cybersecurity firm). The hackers “can leverage this access for follow-on operations, such as data exfiltration or encryption, ransomware, and extortion,” according to an advisory co-authored by the Federal Bureau of Investigation (FBI), the Cybersecurity and Infrastructure Security Agency (CISA), the Australian Cyber Security Centre (ACSC), and Britain’s National Cyber Security Centre (NCSC).
In a separate blog post, Microsoft said that six distinct groups linked to Iran were deploying ransomware, which often encrypts data until a victim sends payment to the hackers. The company warned that Iranian capabilities had improved since September 2020. “As Iranian operators have adapted both their strategic goals and tradecraft, over time they have evolved into more competent threat actors capable of conducting a full spectrum of operations,” Microsoft said on November 16.
June 1, 2022 – FBI Director Christopher Wray alleged that Iran-backed hackers targeted Boston Children’s Hospital in “one of the most despicable cyberattacks” he has seen. Hackers attempted to infiltrate the facility’s computer network in June 2021, but the FBI warned the hospital, then helped identify and mitigate the threat in time. “Quick actions by everyone involved, especially at the hospital, protected both the network and the sick kids who depend on it.”
Sept. 9, 2022 – The United States sanctioned Iran’s intelligence ministry and minister for cyberattacks against the United States and its allies. “Iran’s cyberattacks targeting civilian government services and critical infrastructure sectors can cause grave damage to these services and disregard norms of responsible peacetime state behavior in cyberspace,” Secretary of State Antony Blinken said in a statement.
April 18, 2023: Microsoft warned that an Iran-linked hacking group, Mint Sandstorm (previously dubbed Phosphorus), had started targeting critical U.S. infrastructure including energy companies, transit systems and seaports in 2021. The group gained access to sensitive systems “in support of retaliatory destructive cyberattacks,” according to Microsoft. “The increased aggression of Iranian threat actors appeared to correlate with other moves by the Iranian regime under a new national security apparatus, suggesting such groups are less bounded in their operations.”
April 25, 2023: Iranian hackers had gained access to a local government website that was due to report November 2020 election results, U.S. Cyber Command revealed. But the attack, which was detected by the military, was foiled before the votes were counted with assistance from the Department of Homeland Security. “It could make it look like the votes had been tampered with,” Maj. Gen. William J. Hartman, commander of the Cyber Command’s Cyber National Mission Force, said at a conference.
Andrew Hanna, a program specialist at the U.S. Institute of Peace, assembled this report. Garrett Nada, managing editor of "The Iran Primer," has provided updates.