On September 17, the Treasury sanctioned two groups for cyber espionage. The new sanctions covered Rana Intelligence Computing Company, an Iranian cyber firm, and a cyber espionage group dubbed “Advanced Persistent Threat 39 (APT 39)” by U.S. cyber security companies. The Treasury also designated 45 individuals employed by Rana. All were allegedly working – directly or indirectly – for the Ministry of Intelligence and Security (MOIS).
As of September 2020, Iranian was running cyber operations in at least 45 countries across the Middle East, Africa, Asia, Europe and North America, the State Department said. Iran’s past cyber activities have allegedly included spying on political opposition abroad, taking down U.S. bank websites, setting off an explosion at a Saudi petrochemical plant, and extorting U.S. cities to regain their access to government files.
The latest hackers sanctioned by the United States targeted Iranian dissidents, international airlines and U.S. travel agencies. At least 15 U.S. companies were compromised by Iranian hackers, the FBI charged. Treasury Secretary Steven Mnuchin warned that Iran was determined to “inflict damage on the international travel sector” through cyberattacks.
Rana was “owned or controlled” by MOIS, the Treasury claimed. Iran used Rana to spy on Iranian citizens and install malware installed on their computers. Some targets were later arrested by MOIS and subjected to “physical and psychological intimidation,” Secretary of State Mike Pompeo said in a statement. Rana’s targets included:
- Political dissidents
- Journalists
- Former government employees
- Environmentalists
- Refugees
- University students and faculty
- International NGOs
The Treasury designated 45 Rana employees – managers, programmers and hacking experts – who allegedly helped carry out the cyberattacks. “Iran’s MOIS, through their front company Rana, recruited highly educated people and turned their cyber talents into tools to exploit, harass, and repress their fellow citizens and others deemed a threat to the regime,” FBI Director Christopher Wray said.

The U.S. cybersecurity firms have long suspected APT 39, the sanctioned hacker group, of ties to Iran. Its real name is not known, but it has been active since at least 2014. APT 39 has stolen personnel and private business information from telecommunications companies and airlines. It has also been given other names— including Remix Kitten, Remexi, Cadelspy, Chafer, Cobalt Hickman and ITG07—by U.S. cyber experts tracking the group.
APT 39 has targeted or been suspected of cyberattacks against companies and individuals in ten countries according to U.S. cybersecurity firm FireEye:
- Egypt
- Iraq
- Israel
- Jordan
- Kuwait
- Qatar
- Saudi Arabia
- Spain
- United Arab Emirates
- United States
In a separate statement, the FBI published the computer code used by Iran for “computer intrusion activities” in eight cyberattacks. “By making this malicious code public, it will deal a significant blow to the MOIS and mitigate the ongoing victimization of thousands of individuals and organizations around the word,” the FBI said.
The following are statements by the State Department, the Treasury and the FBI on U.S. sanctions against Iranian hackers.
Secretary of State Mike Pompeo: The United States Sanctions Cyber Actors Backed by Iranian Intelligence Ministry
The Islamic Republic of Iran is one of the world’s leading threats to cybersecurity and human rights online. Today, the United States is sanctioning the Iranian cyber threat group Advanced Persistent Threat 39 (APT39), 45 associated individuals, and a front company, Rana Intelligence Company (Rana) pursuant to Executive Order 13553. Together, these groups and individuals targeted at least 15 countries in the Middle East and North Africa, as well as hundreds of individuals and entities in 30 additional countries across Africa, Asia, Europe, and North America. We will continue to expose Iran’s nefarious behavior and impose costs on the regime until they turn away from their destabilizing agenda.
Iran’s Ministry of Intelligence and Security (MOIS) tracks dissidents, journalists, and international companies for the regime. It has recruited cyber threat groups, front companies, and hackers, and has employed malware to target innocent civilians and companies, and advance the regime’s malign agenda around the world. Cyber actors advance Iranian national security objectives and the strategic goals of MOIS by conducting computer attacks and malware campaigns against perceived adversaries, including foreign governments and other individuals the MOIS considers a threat.
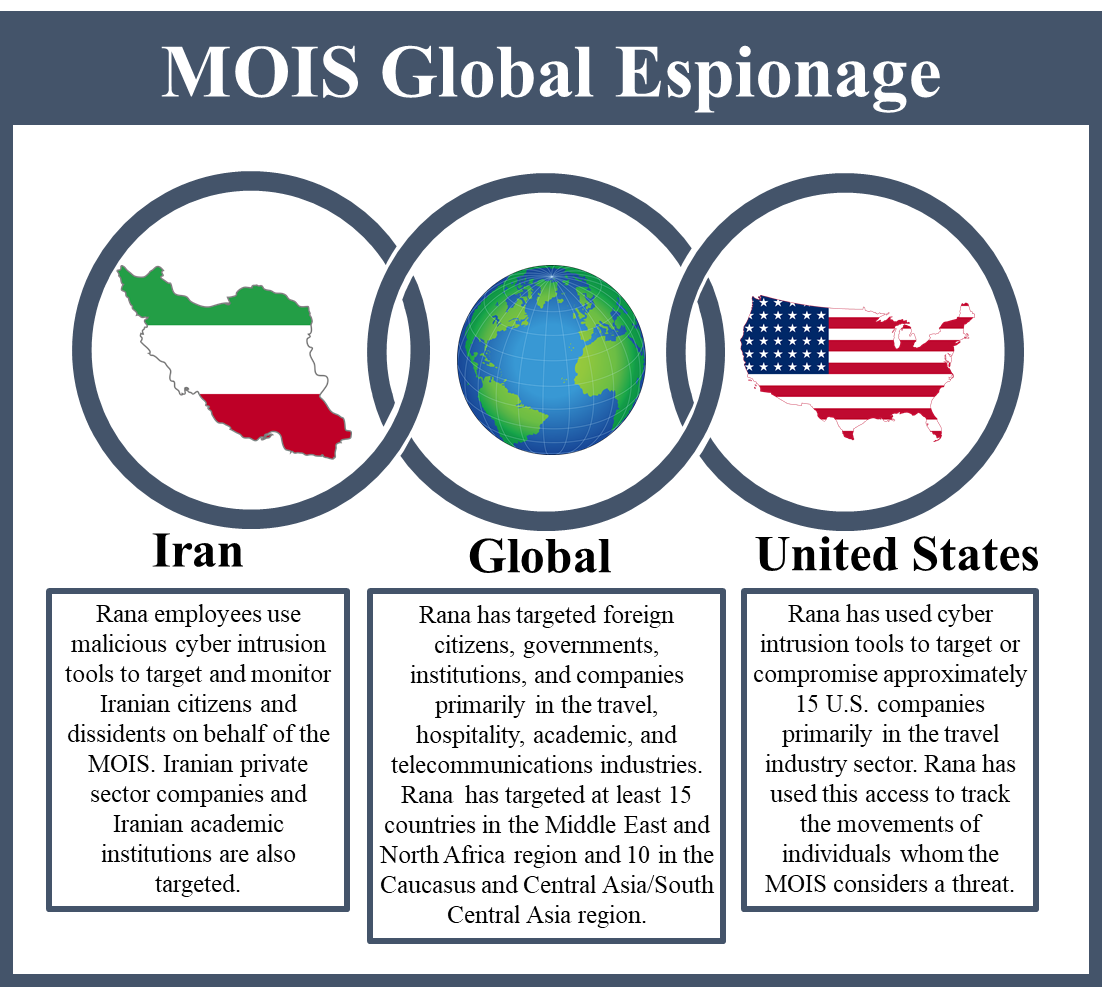
Through Rana, and on behalf of the MOIS, the actors designated today use malicious cyber attack tools to target and monitor Iranian citizens, particularly dissidents, Iranian journalists, former government employees, environmentalists, refugees, university students and faculty, and employees at international nongovernmental organizations. Some of these individuals were subjected to arrest and physical and psychological intimidation by the MOIS.
MOIS actors have also victimized Iranian private sector companies and domestic and international Persian language and cultural centers. Today’s action is another reminder of the great risk that the Iranian regime poses to international cyber security as well as to the Iranian people, who face the continued threat of digital darkness and high-tech silencing. The United States will not relent in our efforts to expose these threats and protect our homeland and our friends and allies.
rests in property of designated or otherwise blocked persons. The prohibitions include the making of any contribution or provision of funds, goods, or services by, to, or for the benefit of any blocked person or the receipt of any contribution or provision of funds, goods or services from any such person.
Department of the Treasury: Treasury Sanctions Cyber Actors Backed by Iranian Intelligence Ministry
Today, the U.S. Department of the Treasury’s Office of Foreign Assets Control (OFAC) imposed sanctions on Iranian cyber threat group Advanced Persistent Threat 39 (APT39), 45 associated individuals, and one front company. Masked behind its front company, Rana Intelligence Computing Company (Rana), the Government of Iran (GOI) employed a years-long malware campaign that targeted Iranian dissidents, journalists, and international companies in the travel sector. Concurrent with OFAC’s action, the U.S. Federal Bureau of Investigation (FBI) released detailed information about APT39 in a public intelligence alert.
“The Iranian regime uses its Intelligence Ministry as a tool to target innocent civilians and companies, and advance its destabilizing agenda around the world,” said Treasury Secretary Steven T. Mnuchin. “The United States is determined to counter offensive cyber campaigns designed to jeopardize security and inflict damage on the international travel sector.”
These individuals and entities were designated pursuant to Executive Order (E.O.) 13553.
Rana advances Iranian national security objectives and the strategic goals of Iran’s Ministry of Intelligence and Security (MOIS) by conducting computer intrusions and malware campaigns against perceived adversaries, including foreign governments and other individuals the MOIS considers a threat. APT39 is being designated pursuant to E.O. 13553 for being owned or controlled by the MOIS, which was previously designated on February 16, 2012 pursuant to Executive Orders 13224, 13553, and 13572, which target terrorists and those responsible for human rights abuses in Iran and Syria, respectively.
Rana is being designated pursuant to E.O. 13553 for being owned or controlled by MOIS. Forty-five cyber actors are also being designated pursuant to E.O. 13553 for having materially assisted, sponsored, or providing financial, material, or technological support for, or goods or services to or in support of the MOIS. The identification of these individuals and their roles related to MOIS and APT39 comes as the result of a long-term investigation conducted by the FBI Boston Division.
The 45 designated individuals served in various capacities while employed at Rana, including as managers, programmers, and hacking experts. These individuals provided support for ongoing MOIS cyber intrusions targeting the networks of international businesses, institutions, air carriers, and other targets that the MOIS considered a threat.
The FBI advisory, also being released today, details eight separate and distinct sets of malware used by MOIS through Rana to conduct their computer intrusion activities. This is the first time most of these technical indicators have been publicly discussed and attributed to MOIS by the U.S. government. By making the code public, the FBI is hindering MOIS’s ability to continue their campaign, ending the victimization of thousands of individuals and organizations around the world.
“The FBI, through our Cyber Division, is committed to investigating and disrupting malicious cyber campaigns, and collaborating with our U.S. government partners to impose risks and consequences on our cyber adversaries. Today, the FBI is releasing indicators of compromise attributed to Iran’s MOIS to help computer security professionals everywhere protect their networks from the malign actions of this nation state,” said FBI Director Christopher Wray. “Iran’s MOIS, through their front company Rana, recruited highly educated people and turned their cyber talents into tools to exploit, harass, and repress their fellow citizens and others deemed a threat to the regime. We are proud to join our partners at the Department of Treasury in calling out these actions. The sanctions announced today hold these 45 individuals accountable for stealing data not just from dozens of networks here in the United States, but from networks in Iran’s neighboring countries and around the world."
The MOIS, camouflaged as Rana, has played a key role in the GOI’s abuse and surveillance of its own citizens. Through Rana, on behalf of the MOIS, the cyber actors designated today used malicious cyber intrusion tools to target and monitor Iranian citizens, particularly dissidents, Iranian journalists, former government employees, environmentalists, refugees, university students and faculty, and employees at international nongovernmental organizations. Some of these individuals were subjected to arrest and physical and psychological intimidation by the MOIS. APT39 actors have also victimized Iranian private sector companies and Iranian academic institutions, including domestic and international Persian language and cultural centers. Rana has also targeted at least 15 countries in the Middle East and North Africa region.
Rana’s targeting has been both internal to Iran and global in scale, including hundreds of individuals and entities from more than 30 different countries across Asia, Africa, Europe, and North America. Rana has used malicious cyber intrusion tools to target or compromise approximately 15 U.S. companies primarily in the travel sector. MOIS cyber actors targeted a wide range of victims, including global airlines and foreign intelligence services. The unauthorized access obtained by the individuals designated today allow the MOIS to track individuals whom it considers a threat.
As a result of today’s action, all property and interests in property of the individuals and entities above, and of any entities that are owned, directly or indirectly, 50 percent or more by them, individually, or with other blocked persons, that are in the United States or in the possession or control of U.S. persons, are blocked and must be reported to OFAC. Unless authorized by a general or specific license issued by OFAC or otherwise exempt, OFAC’s regulations generally prohibit all transactions by U.S. persons or within (or transiting) the United States that involve any property or interests in property of designated or otherwise blocked persons. The prohibitions include the making of any contribution or provision of funds, goods, or services by, to, or for the benefit of any blocked person or the receipt of any contribution or provision of funds, goods or services from any such person.
Federal Bureau of Investigation: FBI Releases Cybersecurity Advisory on Previously Undisclosed Iranian Malware Used to Monitor Dissidents and Travel and Telecommunications Companies
Today, the Federal Bureau of Investigation released a new cybersecurity advisory to academic, public, and private sector partners across the country about previously undisclosed malware attributed to Iranian nation state actors publicly known as Advanced Persistent Threat 39 (APT 39), Chafer, Remexi, Cadelspy, or ITG07. The goal is to make everyone aware of the threat and provide them with the necessary tools to defend their computer networks and mitigate this malicious cyber activity that has already cost companies in the United States and around the world millions of dollars.
Masked behind its front company, Rana Intelligence Computing Company (Rana), the Government of Iran’s Ministry of Intelligence and Security (MOIS) has employed a years-long malware campaign that targeted and monitored Iranian citizens, dissidents, and journalists, the government networks of Iran’s neighboring countries, and foreign organizations in the travel, academic, and telecommunications sectors. Some of these individuals were subjected to arrest and both physical and psychological intimidation. Through Rana, the MOIS also targeted some of the world’s largest travel services companies based here in the U.S. which store the records of millions of travelers. At least 15 U.S. companies were compromised by Rana’s malicious cyber intrusion tools, all of which the FBI has notified, along with hundreds of individuals and entities from more than 30 different countries across Asia, Africa, Europe, and North America.
In the advisory, the FBI is releasing eight separate and distinct sets of malware used by Rana (MOIS) to conduct their computer intrusion activities. Until now, most of these technical indicators have never been publicly discussed, nor attributed to the MOIS by the U.S. government. It is anticipated that by making this malicious code public, it will deal a significant blow to the MOIS and mitigate the ongoing victimization of thousands of individuals and organizations around the world, while also imposing risk and consequences on our cyber adversaries.
The release of this malware, coupled with the sanctions imposed today by the U.S. Department of Treasury’s Office of Foreign Assets Control (OFAC) against Rana and 45 individuals, many of whom were acting as managers, programmers, or hacking experts, is the result of a long-term investigation by the FBI Boston Division.
“These were calculated attacks by a group of individuals with ties to Iran’s Ministry of Intelligence and Security who were intent on harming America and its allies. Today, not only are we publicly identifying them for the first time, but as part of the FBI’s ongoing commitment to our academic, public, and private sector partners, we’re sharing this information with them so they can prevent malware attacks and further victimization,” said Joseph R. Bonavolonta, Special Agent in Charge of the FBI Boston Division.
Photo credits: All photos via Treasury Department (Public Domain)
Andrew Hanna, a research analyst with the United States Institute of Peace, assembled this report
